Judge swamped, justice delayed
TRIAL OF CHIRANUCH PREMCHAIPORN DELAYED UNTIL FEBRUARY 14, 15, 16, 2012.
The third and final act in the trial of the webmaster of independent news portal Prachatai, Chiranuch Premchaiporn, was scheduled for four days this week with expert witnesses for the defence.
Chiranuch’s prosecution for ten pseudonymous comments to Prachatai’s public webboard alleged to be lèse majesté has been the subject of great international interest, both by media and foreign diplomats.
Thai government is seeking to expand its enforcement definitions for what actually constitutes computer ‘crimes’ to include third-party intermediary criminal liability.
A successful prosecution and a guilty verdict would enable government to prosecute such parties as web hosts such as Prachatai, ISPs and even search engines in effect chilling free speech on the Internet.
Chiranuch’s is the first such case to be subject to the benefits of a complete defence on this issue before Thai courts. Her verdict will have deep implications for freedom of the press and free expression in Thailand for the foreseeable future. It is also expected to bear implications for similarly profligate prosecutions by foreign repressive governments against their own citizens.
Observers of the trial of Chiranuch Premchaiporn hoped to see her case concluded at the close of this week and have a verdict before King Bhumibol’s birthday December 5. However, Themis, the ancient goddess of blind justice, appears to have been trumped by Mother Nature.
Readers in Thailand will be aware that there have been areas of extensive flooding in the capital. TV news reports over the weekend showed Rachadapisek more river than road with a backdrop of Thailand’s national courts.
The Thai Cabinet was considering declaring a flood holiday during this week’s final three workdays
Presiding judge Kampot Rungrat was late to court this Tuesday morning because his Chao Phraya riverside home on Koh Kret, Nonthaburi was flooded despite two metres of sandbags. This made surrounding roads all but impassable with water levels expected to rise over the next days.
Judge Kampot only agreed to preside over today’s court session because Danny O’Brien, expert Internet witness for the defence, had travelled to Thailand from the United States for the second time to testify at great inconvenience and expence.
The interpreter provided by the courts of justice stated he was “not a professional” so translations into Thai were facilitated by an accredited and facile interpreter for the defence.
Despite the fact that Chiranuch herself told the court that further elaboration might be gained from Danny’s oral testimony, Judge Kampot ruled that the witness’ written submissions should be sufficiently explanatory. The judge was interested in current accepted legal liability in other countries though he said this may not be applicable in Thai law.
He was interested to hear the future testimony of Thai academic defence witnesses regarding webboard practices and usage when court resumes.
Although Cabinet was considering a flood holiday for the remainder of this week, Thai Parliament will cancel all its legislative sessions through Monday. Presumably, Thai courts will continue to grind exceeding fine except in Judge Kampot’s courtroom where justice has again ground to an abrupt halt.
Three further days of defence testimony will be heard Tuesday, February 14, 2012 and continue on February 15 and 16.
Although the public prosecutor claims he doesn’t “even know how to turn on a computer”, Judge Kampot Rungrat has a Facebook page. In this long hiatus of justice delayed, readers may wish to ‘follow’ him:
https://www.facebook.com/profile.php?id=100001134127083
WHEN COURT RESUMES IN FEBRUARY, WE URGE ALL READERS TO SPEND AT LEAST ONE MORNING OR AFTERNOON SESSION TO SUPPORT JIEW AND TO STAND UP FOR FREE SPEECH.
WE LOVE JIEW! WE LOVE PRACHATAI!
CJ Hinke
Freedom Against Censorship Thailand (FACT)
[FACT comments: We like Danny O’Brien. He has presented the kind of precise critical thinking necessary to any country governed by rule of law. There has certainly been no prosecution witness who demonstrated such deep and unequivocal understanding of how the Internet works and why Chiranuch Premchaiporn is simply not guilty. FACT urges the presiding trial judge to carefully consider this crucial evidence. You public readers now have the essential facts in your hands regarding intermediary liability—you decide. FACT emphasis provided below.]
WRITTEN SUBMISSION BY INTERNET EXPERT, DANNY O’BRIEN, COMMITTEE TO PROTECT JOURNALISTS
My name is Danny O’Brien.
I have worked as a journalist and analyst of Internet technologies since 1994. My work has included testimony before the California Senate on Electronic Commerce on the neutrality of electronic mail (1), the European Parliament on filtering standards (2), and the UK select committee on e-commerce regarding the use of online encryption (3). I have also worked in the Internet and new media industries, as a founding producer at Virgin Media (then Virgin.net), and the UK Guardian’s New Media Lab.
I currently work as Internet advocate at the Committee to Protect Journalists, an independent, nonpartisan organization dedicated to defending the rights of journalists worldwide.
This Statement provides a description of the structure of the Internet where it may affect the accurate determination of intermediary support and consent to the import of illicit materials online (Section 1).
It includes illustrations of Internet intermediary liability in other legal systems (Section 2).
It contains a discussion of the application of the metaphors of “publisher” and “editor” to the provision of websites and webpages (Section 3).
It includes an outline of potential risks regarding ensuring the veracity of digital evidence (Section 4).
It is my belief that these facts have direct relevance to the current case, as provided in Section 5, and summarized in the conclusion to this document.
This information may assist the court in reaching a decision which is fair and consistent with natural justice, and which defines a clear and achievable standard of intent under the Thai Computer Crimes Act, as well as providing a clear guidance to individuals and businesses operating online.
Section 1. Structure of the Internet
Historically, mass communication involved a publisher distributing a number of copies of a publication, or a broadcaster sending a single signal to many receivers.
The Internet operates in a different way. The difference permits it to seamlessly offer both private, individual communications, as well as mass broadcast and publication, to all its users. It allows anyone, not just specific publishers or readers, the capability to communicate to wide or narrow audiences, whether it is to millions or a single person. It also requires the automated transmission and re-transmission of content by many intermediaries without their interference or close examination.
This structure of the Internet is shown in Figure 1. In this diagram, each square is a computer. One computer might serve as a “web host” which provides web pages to those who request them. Another might be an “end-user”, who uses software to ask for web pages, which are then displayed on their own computer screen.
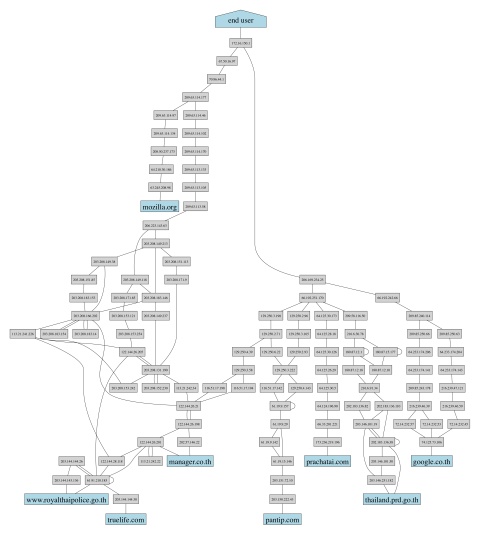
Figure 1. Internet transit paths from a number of web host computers (including Prachatai) to and from a single end-user’s computer. Each intervening rectangle shows a computer that passes, and potentially stores, the data. The end user may be a browser, or a contributor to the web hosts.
On the Internet, data is not sent directly from the sending computer to the receiver. Instead, all digital information, including requests and answers, is sent via many other computers, which collect, save, and re-direct this data.
Traffic between a web surfer and a web site may go over dozens of intermediary computers before it reaches its final destination.
Some of these intermediary computers, called routers, act as traffic police, redirecting traffic between potential destinations. Others may temporarily store data before passing it on, in order to provide a faster local copy (called caches, or caching proxies). Others may block or defend against unwanted data and connections: these intermediaries are often called firewalls.
The data sent and received over this net of computers does not just consist of web pages. It can be email, or online text chat, or video, or online telephone or video chat services like Skype.
Each of the computers situated between one particular sender and receiver copy and forward the data that is being sent. Copying is fast, cheap, and digitally perfect on the Internet. It is only through making multiple copies of data across multiple computers that data gets from one part of it to the other. On the Internet, transmission is largely a matter of making copies.
Most, but not all, of these copies are extremely transitory, and only held for a matter of microseconds. Local Internet providers (Internet Service Providers, or ISPs) may cache copies of far-away web pages for their local users, to decrease delays re-accessing the same content (4). Copies of whole websites may be kept locally on hard-drives. E-mail services may temporarily store emails as they wait for their recipients to download or read them.
Copies of information can even be made locally without users being aware of it. Your personal computer may request, and save locally information that you have not specifically requested. Examples of this are “RSS readers”, which automatically obtain updated content from websites, or unwanted email that is sent to your account without your prior permission, but is still downloaded to your own computer.
These duplicate copies may be available, even after the original content is deleted (5). For instance, local ISP caches may contain website content that has been removed from its original location. Caches like those kept at Google (6, 7) and the Internet Archive can collect, store and display content for months or years after its original provider has gone offline.
Section 2. International standards of intermediary liability
In most jurisdictions, liability has traditionally been attached to possession and/or distribution of unlawful material, with distribution assumed to be closely associated with deliberate intent.
On the Internet, there are potentially many intermediaries automatically redistributing content. All of them may possess vast amounts of data, and redistribute it to other users, without knowledge of what they are storing or redistributing.
This applies equally to websites such as Facebook or YouTube, who deal with billions of messages and videos every day, hosting providers which host thousands of computers delivering websites, and ISPs, who cache and relay content to end-users.
If anyone who possesses or distributes unlawful content is liable per se, the moment that they come into possession, or the moment they import or export such data, then all these groups are liable.
As the Asia Internet Coalition explained in their statement (8) regarding this potential interpretation of the Computer Crimes Act:
“By holding an intermediary liable for the actions of its users, this case could set a dangerous precedent and have a significant long-term impact on Thailand’s economy. It could also end up denying Thai Internet users access to many of the online services they use everyday. Intermediaries, basically any online platform that allows users around the world to connect, such as social networks, online marketplaces and web forums, are a critical component of the Internet today.
Even individual Internet customers may relay and redistribute content without knowledge.
Major services like Skype, BitTorrent, and Spotify (9) all provide software that uses its customers’ Internet connection to redistribute content, without those users being aware of what content is resent. Malicious software operated remotely by criminals may commandeer home computers to download or send spam without users being aware of the process (10).
Some have suggested that if intermediaries wish to avoid liability, they could check or filter content before passing it on. While this model makes sense for traditional publishing platforms, on the Internet all communications are imported and exported at great speed through many unrelated intermediaries.
If all of these intermediaries had a responsibility to check the legality of what they relayed, the entire Internet would grind to a halt. It would be structurally equivalent to making the telephone company liable for any statements made by its subscribers over the telephone, or making restaurant owners liable for what was said at their tables.
This contrast between the enormous amount of automated copying, redistribution and storage that the Internet requires and the traditional attaching of mens rea or intent to possessing or redistributing copies has led to statutory or interpretive changes in the statutory distribution of liability for illicit content in most countries.
Some common themes in these statutory adaptations are:
Liability is concentrated with the original provider of the information.
For instance, in the United States, the Communications Decency Act, Section 230, states outright: “No provider or user of an interactive computer service shall be treated as the publisher or speaker of any information provided by another information content provider.” (11)
In this case, interactive computer service is defined as “any information service, system, or access software provider that provides or enables computer access by multiple users to a computer server, including specifically a service or system that provides access to the Internet and such systems operated or services offered by libraries or educational institutions.”
Information content provider is defined as “any person or entity that is responsible, in whole or in part, for the creation or development of information provided through the Internet or any other interactive computer service.”
This regulation has been subsequently interpreted as granting protection from liability to ISPs, hosting providers, and hosts of discussion forums, against a variety of claims, including negligence, fraud, violations of [US] Federal civil rights laws, and defamation.
No general obligation to monitor
In Europe, the equivalent law, the e-Commerce Directive (12), provides explicit blanket liability protection for some specific intermediary activities, including caching, hosting, and “mere conduits” such as Internet Service Providers (13).
There is also a wider prohibition on requiring intermediaries to monitor or pro-actively seek out illegal activity on their networks. (14)
Liability dependent on knowledge and reaction
The e-Commerce Directive provides immunity to service providers hosting illegal material, provided that they have no actual knowledge of the content and expeditiously remove the content if the service provider once made aware of its status; in the U.S., the protection continues to protect intermediaries even subsequent to the notification of illegal content.
Section 3. Websites, Publications, and Publishers
It has been implied in the current case website providers have some additional responsibility for what appears on their pages, in the same way that a newspaper publisher or editor might be assumed to have liability for the opinions expressed within the pages of their publication. The apparently similarity between a web page and the page of a newspaper and a magazine is, however, deceptive.
A complete web page is only created for display by the end-user’s browsing software. The final “page” is actually made from many disparate parts, served by many different computers, owned by different organizations.
Figure 2 shows a sample web page from www.bangkokpost.com, together with the sources of its various elements. Many different computers, under the control of entirely different groups, might contribute to the overall appearance of a site. Also, a site will often have links, which point to content hosted on other systems.
 Figure 2. A screenshot of popular website, www.bangkokpost.com . Each of the numbered elements of the page is loaded by the end-user from web hosts other than www.bangkokpost.com. Some are controlled and maintained by the Bangkok Post, many are not. 1) Image loaded from Truehits (lvs.truehits.in.th), 2) Flash movie loaded from another Bangkok Post computer (ads.bangkokpost.co.th) 3) Advertisement from Google Inc (googlesyndication.com), 4) Text and graphics from Siam Commercial Bank (scb.co.th), 5) Text and graphic from Stock Exchange of Thailand (settrade.com).
Figure 2. A screenshot of popular website, www.bangkokpost.com . Each of the numbered elements of the page is loaded by the end-user from web hosts other than www.bangkokpost.com. Some are controlled and maintained by the Bangkok Post, many are not. 1) Image loaded from Truehits (lvs.truehits.in.th), 2) Flash movie loaded from another Bangkok Post computer (ads.bangkokpost.co.th) 3) Advertisement from Google Inc (googlesyndication.com), 4) Text and graphics from Siam Commercial Bank (scb.co.th), 5) Text and graphic from Stock Exchange of Thailand (settrade.com).
It is possible for a web page’s content or context to be radically changed by having any of these external parties independently change the content they are providing. They can do this at any time, with no control from the web page’s apparent operator. The source of an image on a web page might change it from a cat to a horse, without permission from the owner of the website server. A web link to an innocuous audio file could be changed to direct the user to unlawful content, even after the content had been inspected for moderation by an administrator.
Content can also be presented differently depending on the viewer. Someone posting an external image of a cat on a discussion board could change it to a horse when viewed by someone from a particular location, or serve a different file from a hyperlink depending on who was clicking on the link.
Web pages are far more than just static pages containing texts and pictures created by the website’s host. They are the vessels which hold almost all the other forms of interactive activity that the Net makes possible. Portions of web pages can be used for streaming video, live audio chat, telephone calls, and textual discussion.
A single web page can be part traditional news service, part discussion area, part telephone conversation. For instance, Facebook.com offers instant messaging, video and discussion forums, all on one page. (See Figure 3.)
 Figure 3. A Facebook web page, showing video and instant messaging, as well as discussion.
Figure 3. A Facebook web page, showing video and instant messaging, as well as discussion.
In particular, news services frequently offer a live user commentary service on the same page, as managed, edited content. Such content may be automatically relayed using a completely different editorial system to the managed content, as was the case with Prachatai’s message board.
Section 4. Standards of Evidence
As a consequence of the features of web pages described Section 3, websites and other online services can appear very differently depending on how and where they are accessed. The elements of even a single web page will almost certainly not be delivered from s single location or owner.
The web page may not even be delivered from its apparent location at all. An example of this are web pages that are blocked by the MICT.
In these cases, a request to access a particular web page hosted at, say Wikipedia, will instead deliver a message prepared by the MICT. This message only occur for users accessing the website in Thailand, and will appear to come from Wikipedia’s server, even though it is delivered by local Thai ISPs (15).
For these reasons, it is impossible to reconstruct from simple illustrations of a computer screen, or screenshots, the origins and path of a single webpage.
For proof beyond reasonable doubt that a web page or other content has been sent from a particular server, and not originated by other servers or interfered with en route, the following evidence would be required:
1) In the case of a web page, the “HTML source” of the page, which lists the elements of a web page, including their original sources.
2) Logs from either the originating server, or a reliable intermediate stage, such as an ISP, showing that the content was originally delivered from these servers.
3) An archived digital copy of the web page, showing the different elements as they were dated and received.
4) A repeated attempt to access the same data, from a different location, unconnected with the investigating party.
Without such logs and recorded data, it is possible for investigators to be misled as to what is viewable by website’s moderators or the general public. All such evidence is obtainable with timely action by law enforcement, and using software which “rips” or archives the complete HTML of a site. [FACT: Will police do this in future?]
In addition, local computers may temporarily cache or store information that has been sent to them without their owners’ permission — for instance, spam email messages or content transmitted via P2P software.
The United States courts have determined that, in general, “the mere existence of an image automatically stored in the cache, standing alone, is legally insufficient to prove either knowing procurement or knowing possession” (16).
Section 5. Application to the current case.
The present case centers around the interpretation of “intentionally supporting or consenting to an offence under Section 14 within a computer system under their control” in Section 14 of the CCA.
The prosecution claims that Chiranuch Premchaiporn is liable for the distribution of content posted to the prachatai.com website by third-parties the moment it appeared, and that liability was not removed when the content was deleted.
Under the current design of the Internet, if “intentionally supporting or consenting” involves merely operating or managing a computer involved as an intermediary in a crime under Section 14, then criminal liability would extend to all intermediary Internet telecommunication providers and hosts, including telecommunication companies, and the providers of Internet connectivity to MICT and its investigators. It seems unlikely that this is the meaning intended by the legislators.
International law places no pre-emptive obligation on intermediaries to monitor content for illicit activity (US: CDA Section 230, EU: e-Commerce Directive ).
Still, if liability is assumed because of a failure to sufficiently police the uploading of third-party content, it is unclear why Ms. Premchaiporn is specifically targeted.
If a mere failure to moderate or block third-party content passing via a computer, triggers liability, again, the same liability extends to all other intermediaries involved in importing the illegal data, including ISPs passing data to the prachatai.com website, or even to MICT censors for failing to block the content in reasonable time.
While Prachatai.com has portions of its content edited with the norms of a traditional editorial processes of a newspaper, in which its editors were aware of, and actively intervened in the structure and content of published articles, the liable comments were provided in a completely different system, far closer to the norms of Internet intermediary relaying.
In a commentary system, the sheer number and interactivity of the number of comments means that editing or oversight in this sense is impossible. Rather than expecting oversight as one might a “letters to the editor” section of a newspaper, it would be akin to live moderation or editing of telephone conversations, or instant messages.
To give some example: the news site The Huffington Post receives 4 million comments per month, or over one every second (17). Twitter, a site for posting short commentary, relays 200 million tweets per day (18) – over two thousand messages a second.
On the popular video posting site, YouTube, 48 hours of video are uploaded every sixty seconds (19).
The roles and responsibilities of editor and publisher in one context are radically different from that of webmaster or host in the other.
Ms. Premchaiporn’s role as a traditional editor in one capacity should not affect whether she is considered as an intermediary in the more widespread sense of an Internet intermediary in another.
The international norms of an editor, webmaster or hosting service of a web discussion forum are to seek out and remove content if notified. A general obligation to monitor is explicitly not required.
Finally, printouts of web pages have limited evidentiary weight in proving the path of the distribution and hosting of content. [FACT: Only screenshots were provided by police.]
They do not demonstrate knowledge of the origin of the content, nor how it may have changed over time or in transit. For a criminal prosecution, a higher standard of proof and digital forensics is attainable, and required.
Conclusions
1. The legal theory presented by the prosecution in this case, namely that Internet intermediaries are instantly liable for all illicit content contained or relayed by their servers, would result in near universal liability online, and place a unsustainable and unjust burden on a broad large class of Internet users, including businesses and individuals with no capability to police or monitor the content passing through their networks.
A free and open Internet is a vital element of a modern free press, and a modern free society.
The witness urges the court to reject this theory in for reasons of natural justice, and the public interest.
2. While a web page may have a superficial resemblance to a “page” of a traditional printed publication, much of its content included and linked to by a page does not and cannot be controlled by the host or publisher in the way that a newspaper publisher or editor oversees or selects content in a traditional publication. Many journalistic organizations operate both editorial content in the midst of other, unmanaged material.
To assume that, because Prachatai operates part of its services as an edited, managed, service, it has a general capability to pre-filter and police content on other parts of its service is an unwarranted step.
In the interests of preventing an unjust burden on media organizations that run traditional, edited, services online, we urge the court to reject this assumption.
3. Criminal liability requires a high evidentiary standard as a matter of course. The multiple-sourced nature of digital content on the Web and the Internet’s many intermediaries mean that the sources, appearance and transmission route of illicit content may not be obvious without intermediate logs and audit trails. Because of the intermediary nature of computers on the Internet, it is also difficult to ascertain whether information stored in temporary caches (such as within email clients) was requested or even seen by the computers’ owner.
In the interests of translating the high standards of evidentiary proof in the court from the analog to the digital world, we urge the court to reject any evidence provided as simple printouts or screenshots without supplemental confirmation of the source and transmission of the content.
1 On the matter of the Goodmail/AOL CertifiedEmail proposal, April 3rd, 2006 http://w2.eff.org/ spam/aolmail/20060403effgoodmailtestimony.pdf
2 Network Filtering: Limiting Cultural Industries, Damaging the Internet, https://www.eff.org/files/filenode/effeurope/NetworkFiltering.pdf
3 STAND submission on E-Commerce, http://web.archive.org/web/20000815071052/http:// www.stand.org.uk/select.html
4 HTTP protocol standard, IETF, https://tools.ietf.org/html/rfc2068#section-13
5 See, for example, “Deleted” Facebook pages may not be deleted, http://arstechnica.com/web/news/2010/10/facebook-may-be-making-strides.ars
6 Browsing the Web using Google Cache, http://googlesystem.blogspot.com/2007/01/browsing-web-using-google-cache.html
7 The Wayback Machine, http://www.archive.org/web/web.php
8 Statement on Computer Crimes Act, http://www.asiainternetcoalition.org/advdoc/8887df8fd914ff2b80829a6a6327e91c.pdf
9 Skype’s customers may relay others phone calls as a “supernode”. BitTorrent users automatically re-distribute the content they are downloading. Spotify, a licensed music service, uses its end-users’ machines as caches for other users. See http://en.wikipedia.org/wiki/Supernode_%28networking%29 , http://en.wikipedia.org/wiki/BitTorrent_%28protocol%29#Description, http://en.wikipedia.org/wiki/Spotify#Technical_function
10 What is a Botnet? Microsoft, http://www.microsoft.com/security/resources/botnet-whatis.aspx
11 47 U.S.C. 230 http://www.law.cornell.edu/uscode/16/230.html
12 E-Commerce Directive, 2000/31/EC, http://ec.europa.eu/internal_market/e-commerce/index_en.htm.
13 2000/31/EC, Art 12,13,14 14 2000/31/EC, Art 15
14 2000/31/EC, Art 15
15 See the last images of the video hosted at: http://www.youtube.com/watch?v=6ToQ4zgQZ_E which shows a MICT block page at a Wikipedia web address.
16 People v. Kent, 2d Dept. 10/12/2010, http://law.justia.com/cases/new-york/appellate-division-second-department/2010/2010-07364.html
17 AOL Buys Huffington Post, http://www.pcmag.com/article2/0,2817,2379559,00.asp
18 Twitter Blog, http://blog.twitter.com/2011/06/200-million-tweets-per-day.html
19 YouTube Blog, http://youtube-global.blogspot.com/2011/05/thanks-youtube-community-for-two-big.html
Prachatai English is an independent, non-profit news outlet committed to covering underreported issues in Thailand, especially about democratization and human rights, despite pressure from the authorities. Your support will ensure that we stay a professional media source and be able to meet the challenges and deliver in-depth reporting.
• Simple steps to support Prachatai English
1. Bank transfer to account “โครงการหนังสือพิมพ์อินเทอร์เน็ต ประชาไท” or “Prachatai Online Newspaper” 091-0-21689-4, Krungthai Bank
2. Or, Transfer money via Paypal, to e-mail address: [email protected], please leave a comment on the transaction as “For Prachatai English”
